SOC 2 Compliance For Security Builds Trust for ScaleUp Growth

Maintaining security, privacy and confidentiality are three of the most pressing challenges tech ScaleUps face today, both internally and for customer data and applications.
In addition to the legal and existential threats that potential cyber attacks pose to organizations, a breach can have significant impacts on customer trust and investor confidence, especially in sectors such as financial technology (fintech), insurance and healthcare. Customers worry about entrusting their data with a vendor that has previously been exposed to attacks, and will want hard proof that your ScaleUp has adequate security policies and protection in place.
Research firm Gartner predicts that by 2025, 60% of businesses will use the thoroughness of a company’s security policy and their cybersecurity risk level as a primary criterion when evaluating business opportunities.
One way to bolster your customers’ trust in your organization’s internal controls and procedures is by meeting compliance measures such as System and Organization Control (SOC) reporting.
Nearly 2,000 breaches on 300 million customers in 2021
Concerns about cyber security are well-founded: 2021 was a record-breaking year for compromised consumer data, according to the Identity Theft Resource Center. Close to 2,000 breaches affected 294 million users last year.
Ransomware is also a growing persistent threat, accounting for 22% of attacks. These attacks can affect almost any system within a company and have recently crippled hospitals, police departments, and schools. Industry research firm Gartner projects that companies will spend over $170 billion annually on security by 2022. Global cybercrime costs could balloon to $10.5 billion by 2025.
Amid this backdrop, securing your services is critical to maintaining customer confidence and safeguarding privacy. Under the SOC umbrella, SOC 2 compliance is more oriented toward security than other SOC audits types. With it, your organization becomes much more reliable in the eyes of your customers.
To be clear, checking off a security compliance list is insufficient for proper security, and over-focus on protocols and compliance can actually detract from key objectives. Yet SOC 2 can extend trust among your customer base and even serve as a selling point for future customers, the biggest and best of whom will require that your ScaleUp has it in order to work with your organization.
What is SOC?
A System and Organization Control (SOC) report is the result of an audit of a company’s internal systems and procedures. The set of guidelines and standards that SOC audits cover are determined by the American Institute of Certified Public Accounting (AICPA).
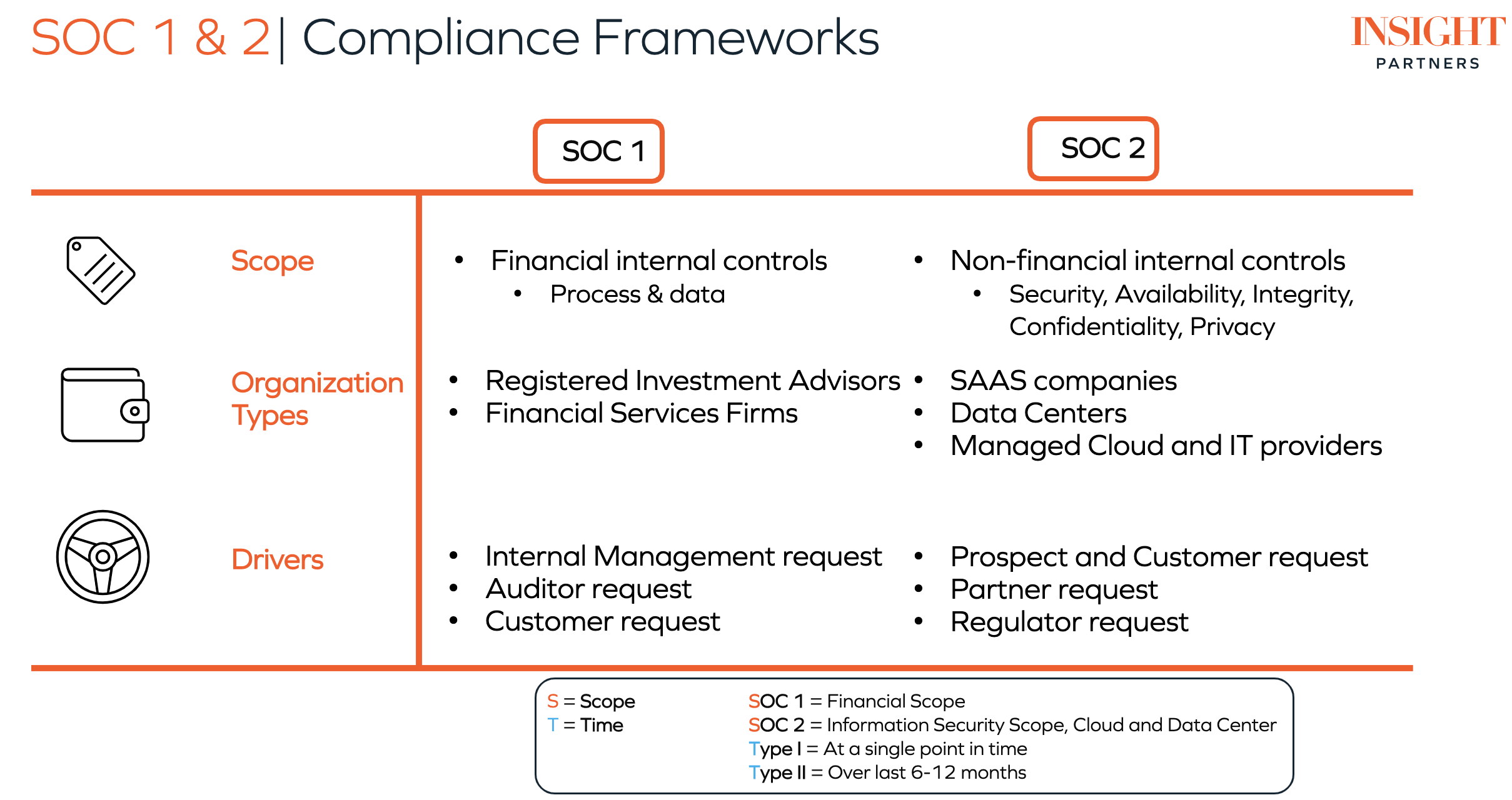
There are three different SOC reports:
- SOC 1 focuses on the internal financial reporting practices of a company.
- SOC 2 covers non-financial security and trust, including data security, privacy and confidentiality.
- SOC 3 focuses on the same areas of compliance as SOC 2, but the report is less detailed, less technical and more suitable for general use.
There are also different types of SOC reports: both SOC 1 and SOC 2 have Type I and Type II reports. In short, SOC 1 and SOC 2 refer to different scopes (material examined), while Type I and Type II for either report refer to different times over which the company is evaluated.
The three reports are not inclusive — achieving SOC 2 compliance does not mean your organization is automatically SOC 1 compliant, and SOC 3 compliance does not automatically guarantee SOC 1 and 2 compliance.
SOC 2 Compliance
Unlike SOC 1, which is most appropriate for companies dealing with large financial transactions, SOC 2 compliance can apply to most (if not all) tech ScaleUps. SOC 2 addresses five categories of trust services: security, confidentiality, privacy, availability and processing integrity.
- Security service controls ensure that your organization has taken adequate steps to prevent data from being accessed by unauthorized individuals.
- Confidentiality practices cover how confidential data is used by the organization, as well as how this data is handled both in transit and at rest (stored in a database or a data lake).
- Privacy controls ensure that your organization maintains policies for what personally identifiable information (PII) is collected from users, how that information is used, which third parties it is given to and that end-users are aware of and consent to the use of their data.
- Availability controls establish whether your company’s systems are available for use by clients as stated in your service-level agreements (SLAs) with clients. This includes factors like disaster recovery and business continuity procedures.
- Processing integrity controls to ensure that your organization’s data processing is accurate and comprehensive and that there are checks in place to identify and correct errors. This can be especially important for ScaleUps that offer services derived from machine learning algorithms for which proper data processing and model tuning are fundamental to the business’s value proposition.
Achieving SOC 2 compliance requires an audit of these five trust services categories by an outside firm and a certified public accountant (CPA), for a period of time determined by whether the company is applying for a Type I or Type II certification. A SOC 2 Type I report examines an organization’s policies and procedures relating to the five trust-service criteria listed above. It is used to evaluate whether they are fit for purpose – that is, whether their design is adequate for the services the company offers. SOC 2 Type I only covers a single point in time and is not used to evaluate whether the policies are actually implemented effectively.
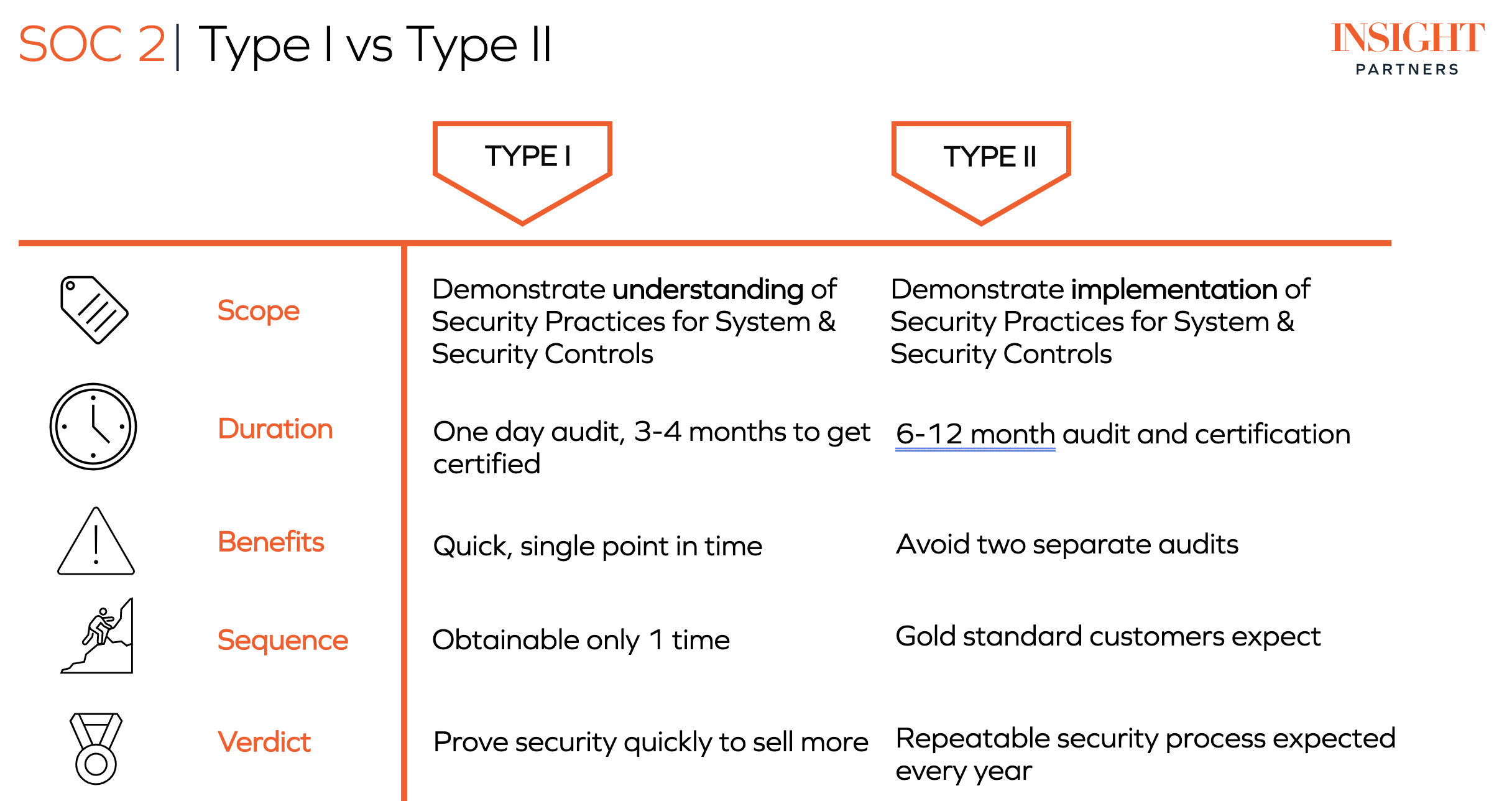
By contrast, a SOC 2 Type II audit verifies not only that the company’s declared practices are appropriate, but that the company follows its own procedures over a period of time (usually six to 12 months). Because of the high value of privacy and security in today’s tech landscape, having a SOC 2 Type II audit can drive significant additional value for a business. The certification that your company consistently and thoroughly implements security, privacy and other SOC 2 policies can boost customer trust, and increase repeat and new business.
Why do I need a SOC 2 audit?
The importance of SOC 2 compliant policies seems obvious in today’s tech landscape. However, tech ScaleUps are also often notoriously focused on product and struggle to prioritize resources to achieve compliance. Prioritizing product features may work in the early stages but is ultimately an unscalable approach.
Tech ScaleUps today live and work in a variety of fields, and the cost of not adopting security and privacy policies that meet SOC 2 standards (in addition to devoting the necessary resources for cyber security in general) can be massive.
Breaches caused by inadequate security often incur financial penalties from regulators. The health-tech space, for instance, boomed in 2020 due to the COVID-19 pandemic, yet also racked up a 10% annual increase in data-breach costs. Healthcare breaches are particularly costly when there is a violation of the Health Insurance Portability and Accountability Act (HIPAA) – the federal law that protects patient privacy and imposes harsh fines on organizations that improperly handle patient data. From a purely financial perspective, the security policies enforced by a SOC 2 audit can prevent your company from hemorrhaging money further down the line.
How Insight Partners can help you get SOC 2
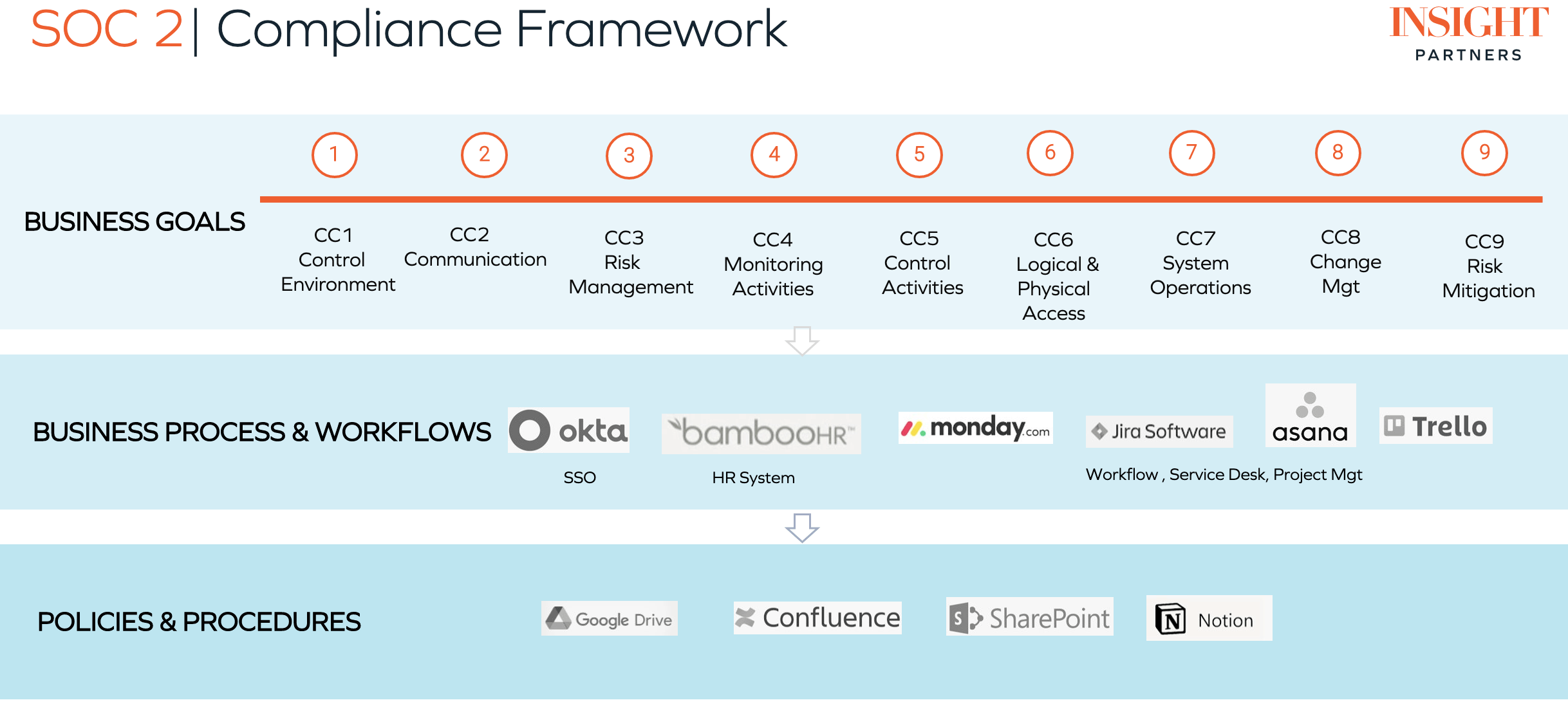
Achieving SOC 2 compliance can be challenging for ScaleUps trying to expand out a product while building a solid foundation of infrastructure and security. Insight Partners provides a number of resources, as well as direct partnerships to help companies on their road to SOC 2 Type I and SOC 2 Type II compliance. The framework below can guide your journey:
For example, portfolio company Vanta offers deep dives into SOC 2 compliance, including best practices to implement.
Perimeter 81’s SOC 2 Type 2 certification verifies that it delivers the highest level of security, privacy and compliance to its clients. A SOC II Type 2 compliant service must follow these five “trust service principles” when managing customer data: Security, availability, processing integrity, confidentiality and privacy. This is critical, since its customers rely on its cloud-delivered network security platform to protect their cloud, on-premises and hybrid environments.
Another example is Amazon Web Services’ SOC report demonstrating how AWS achieves its key compliance controls and objectives for security, availability and confidentiality of its control environment. AWS says the reports are instructive for your organization, and for auditors, by detailing how AWS controls support operations and SOC 2, as well as SOC 1 and SOC 3.
Working with Insight Partners can help your company get to SOC 2 compliance efficiently and ensure that your organization’s security and privacy procedures are able to scale and grow alongside its product. The SOC 2 compliance audit is an investment that ensures your organization and infrastructure is set up to gain trust among your existing and future customer base and consequently, business success.