Why a Lack of Cybersecurity Poses an Existential Threat to Your Business

Fundamental security flaws in technical environments could have a massive impact on the global economy. The World Economic Forum (WEF) estimates a successful cyber breach cost, on average, $3.6 million in 2021. The share price of a hacked company underperforms on the NASDAQ by an average of 3% — even six months after the disclosure of a security breach.
Today, not only are ransomware attacks crippling companies, but a variety of malware is also surreptitiously inserted into software components. Malware is widely employed across thousands of applications, sparking a cybersecurity crisis worldwide.
The attacks already prompted the Biden administration to issue an executive order last May that may have a far-reaching impact. It requires all U.S. federal agencies to share cybersecurity intelligence, adopt cybersecurity best practices, improve the security of software supply chains, automate vulnerability remediations and implement a standard set of incident response workflows.
The U.S. government is mandating the implementation of “zero-trust” IT environments. Naturally, it won’t be too long before enterprise IT organizations of all sizes follow the lead of the U.S. government as they seek the right tools and processes to mitigate the increasingly existential cybersecurity threats.
In today’s cyberthreat landscape, we see three major cybersecurity trends for 2022:
- AI-powered cybersecurity
- Growing threat of ransomware
- IoT vulnerabilities
This article describes the current cyber threat landscape and covers critical actions organizations need to take. Viable solutions that Insight Partners portfolio companies provide are also covered. As you can see, we have a large set of portfolio companies that address all areas of the security spectrum, from threat management to application security to network, IoT, and risk management.
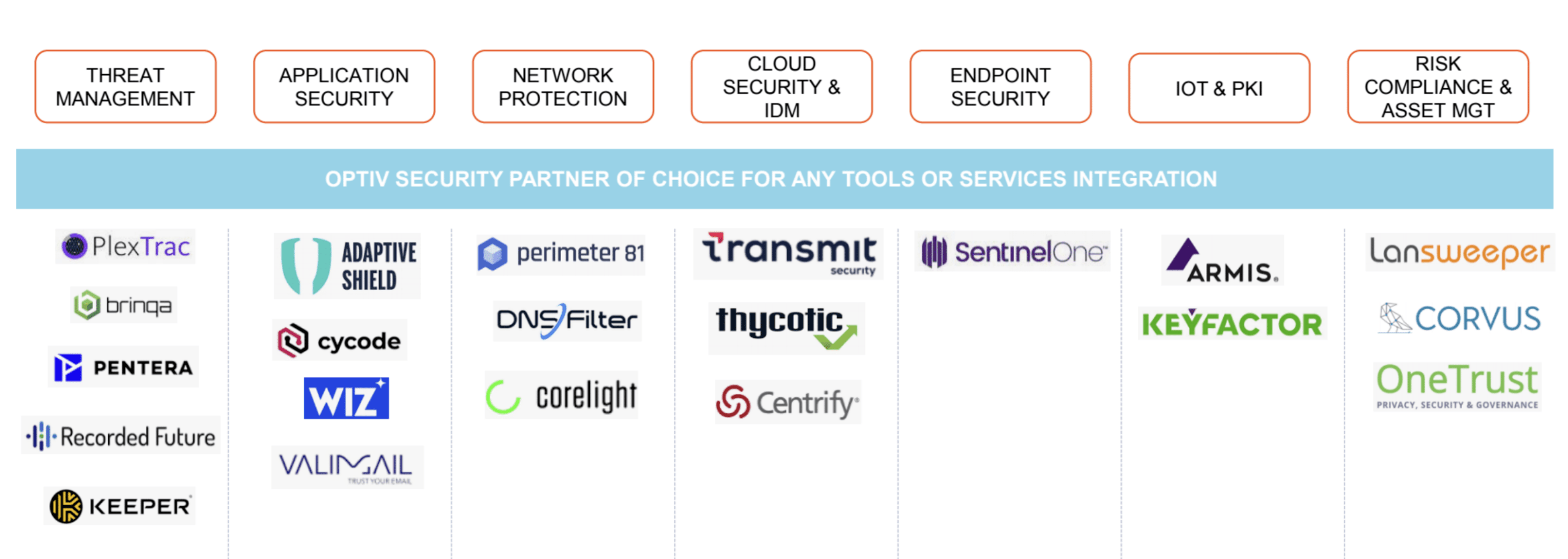
We’re here to partner with you and set up a scalable infrastructure. You can learn from the successes and challenges of other portfolio companies, our partner community and boost innovation through collaborative networks. Security transformation is no longer a bold move — it’s a standard practice in today’s market.
Zero-Trust IT Needs AI
Zero-trust is not a new idea when it comes to cybersecurity. Following a series of high-profile breaches over the past two years, the concept is top of mind.
The approach first surfaced back in 1994, when the National Cyber Security Centre (NCSC) in the U.K and the National Institute of Standards and Technology (NIST) in the U.S. raised awareness of the need for IT systems to not trust any device, application, or individual by default.
The challenge is that zero-trust IT is not something an organization can buy. It describes an architecture that requires the seamless integration of an array of cybersecurity tools and platforms. The issue most organizations immediately encounter is a lack of internal expertise required to actually implement a zero-trust IT environment. There are more than 400,000 open security positions in the U.S. alone, according to Cyberseek.
It’s clear that new approaches to automating cybersecurity will be required to thwart cyberattacks involving, for example, ransomware that are increasing in both volume and sophistication. Accomplishing that goal will require increased reliance on artificial intelligence (AI) to augment chronically short-handed cybersecurity teams.
When AI first arrived on the cybersecurity scene, there was understandably a lot of skepticism. Grandiose claims about the ability of AI platforms to eliminate the need for security analysts have fortunately given way to more rational assertions that focus on the role machine-learning (ML) algorithms will play in augmenting cybersecurity professionals.
AI at its core identifies behaviors that signal antipatterns. AI can process thousands of events taking place every second. One example is our portfolio company, Recorded Future. Their natural language processing capability instantly classifies billions of entities in every language. They automatically map relationships between entities such as companies associated with their products, the type of malware and vulnerabilities exploited, a geographical entity and the city, and country of occurrence. Their Security Intelligence Graph scours a large quantity and variety of sources from the open and dark web, as well as exclusive technical sources, to identify threats.
Ultimately, ML algorithms, for example, will reduce cybersecurity fatigue by eliminating many of the false-positive alerts that overwhelm cybersecurity teams today. ML algorithms can also be applied to the IT environment to identify the relationship between anomalies and alerts.
Ransomware Is Not Going Away
Ransomware attacks are clearly the dominant cybersecurity threat of our times. These attacks are becoming more targeted as cybercriminals become more organized. Advanced persistent threat (APT) groups are now working with cybercriminals that specialize in gaining access to networks or acquiring intelligence as part of a two- or three-pronged attack.
Ransom negotiations are also handled by individuals who act as brokers for various ransomware gangs. The going rate for a ransom these days is over $6 million in the U.S. alone according to email security firm Mimecast, as malware groups look for bigger paydays. In many cases, patient cybercriminals are taking months to observe how organizations operate before launching a ransomware attack and maximizing its devastating impact.
Among the many challenges is how even when law enforcement officials take down one of the ransomware groups, another dozen or more copycats can emerge to take its place. One of the more obvious ways for organizations to avoid being exposed to ransomware attacks is to limit user access to exposed websites and connections.
While this would require a significant amount of resources to manage in-house, our portfolio company DNSFilter serves as a third-party alternative. It has AI-powered security that protects from ransomware at the network level. It blocks known and zero-day ransomware domains to ensure employees do not inadvertently download malware.
IoT Everywhere
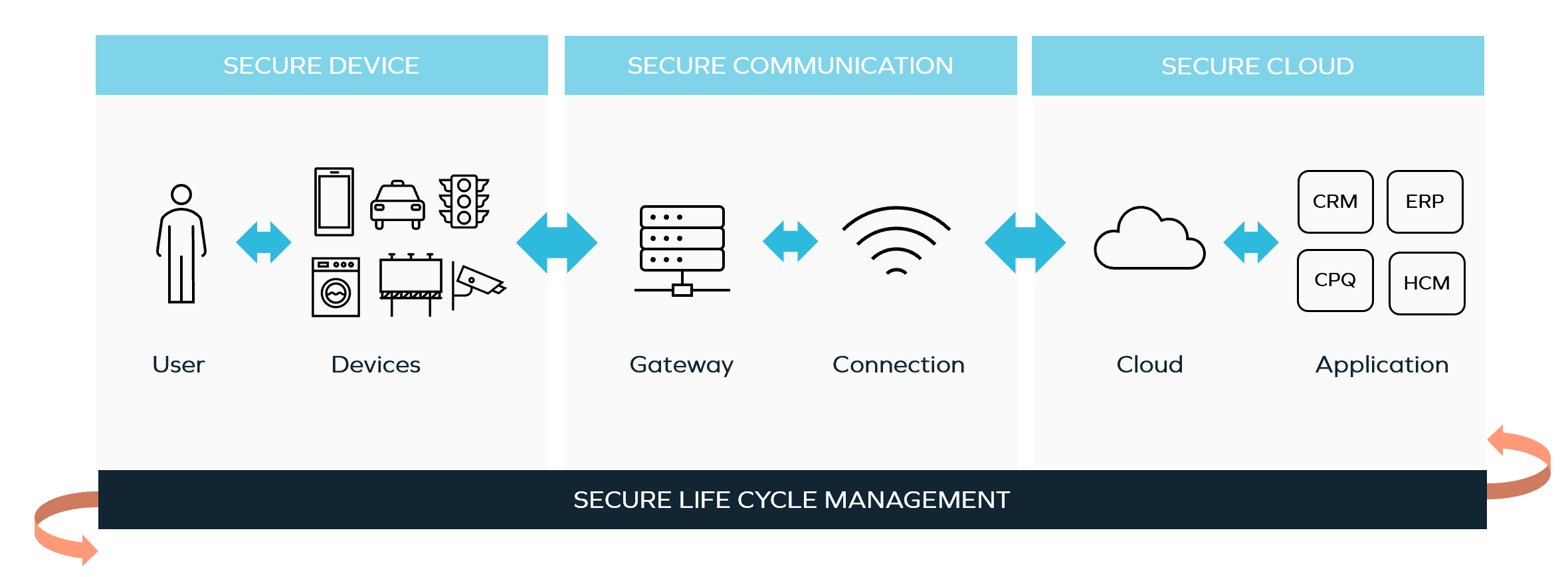
Many critical systems are more vulnerable because they have been connected to the Internet recently, as the Internet of Things (IoT) applications are rolled out to the network edge. According to Statista forecasts, there will be almost 12 billion IoT devices worldwide by the end of 2022 compared to 8.74 billion devices in 2020. The number of IoT devices is expected to continue to surge, totaling 25.4 billion IoT devices in 2030. Cybercriminals use these connected devices in the automotive, healthcare, retail, and building automation industries to gain access to valuable data stored across an extended enterprise. Each of these IoT applications represents yet another gateway through which malware can spread laterally.
Our portfolio company Keyfactor helps address this issue by enabling organizations to automatically find, control and manage machine identities. Keyfactor Control is an end-to-end identity security platform for connected devices that makes it easy and affordable to ensure the trustworthiness of devices and software during manufacturing and the device lifecycle. Keyfactor also enables the management of public key infrastructure (PKI) to ensure the security of the manufacturing supply chain.
Challenging, But Doable
Gartner predicts that by 2025 a full 60% of organizations will use cybersecurity risk as a primary differentiator to determine which organizations they should partner with in order to advance a digital business transformation initiative. Organizations that are unable to meet that bar will likely lose market share.
The best cybersecurity defense, of course, is to implement an end-to-end framework, prioritize controls based on level of risk and likelihood of occurrence, then move quickly to accept, reduce or control gaps.
There is no shortage of platforms that enable organizations to improve their overall cybersecurity posture. The challenge is determining what mix of cybersecurity technologies to employ to achieve that goal.
Since achieving a security transformation has become a standard practice for any organization hoping to avoid putting its survival at risk, we’re here to partner with you during your cybersecurity journey. We can help you set up a sustainable approach and implement a scalable infrastructure plan for improving your overall cybersecurity posture that best meets your organization’s individual needs. By coming aboard, we also offer you the opportunity to learn from the successes and challenges of other portfolio companies and our partner community.
To learn more, click below to read Insight's article, What We’re Hearing from Cybersecurity Leaders.