Security is complex, broad, and five miles deep. Depending on the background of the person in charge of a company’s security it can also be singularly focused and, as a result, introduce risk that could impact company value. Startup software companies focused on building product features may not prioritize security practices, which can jeopardize sustainable growth. ScaleUp companies evolve to make security equally as important as features to protect customers and the business.
Recognizing the need for a comprehensive security framework tailored to scaling software companies, Insight Onsite has reviewed all available industry frameworks and talked to experts. We have synthesized security standards and best practices into an intuitive framework to guide the management of the security practice.
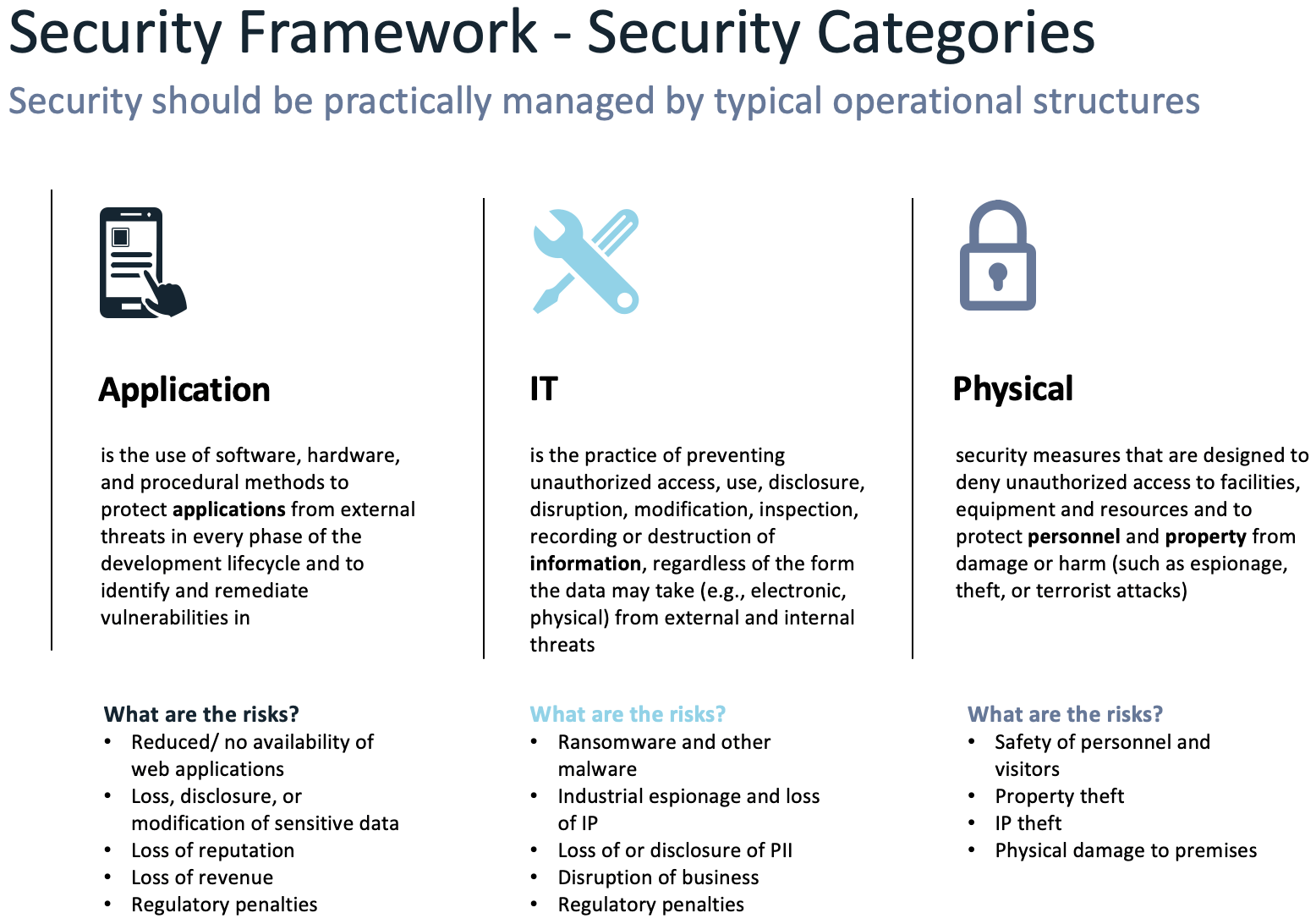
End-to-end security consists of Application, IT, and Physical risk management, an evolution from the early industry starting point of network security. We further break down these high-level categories and assign key activities that de-risk each.
Below is a definition and scope of the three primary categories.
Successful risk management occurs with a “security first” mindset and it takes time to build and embed fundamental security practices in a company. There are critical areas that must first be addressed to set a solid baseline. These are what we term “table stakes” and are defined as the highest priority and fundamental activities that will de-risk Application, IT, and Physical security. The three capability levels for each category (Application, IT, and Physical security) are:
- Table Stakes – this comprises the prioritized key activities within each of the 3 categories that will de-risk company assets and set an end-to-end, baseline security management practice. At a minimum, these must be included in the management of each security category.
- Security Proficiency – these activities improve upon and broaden the fundamentals established in Table Stakes
- Security Maturity – these activities solidify and embed management of best security practices. These activities drive a best-in-class security practice to de-risk your business.
At a minimum, companies should embed the table stakes activities listed below into their security practice:
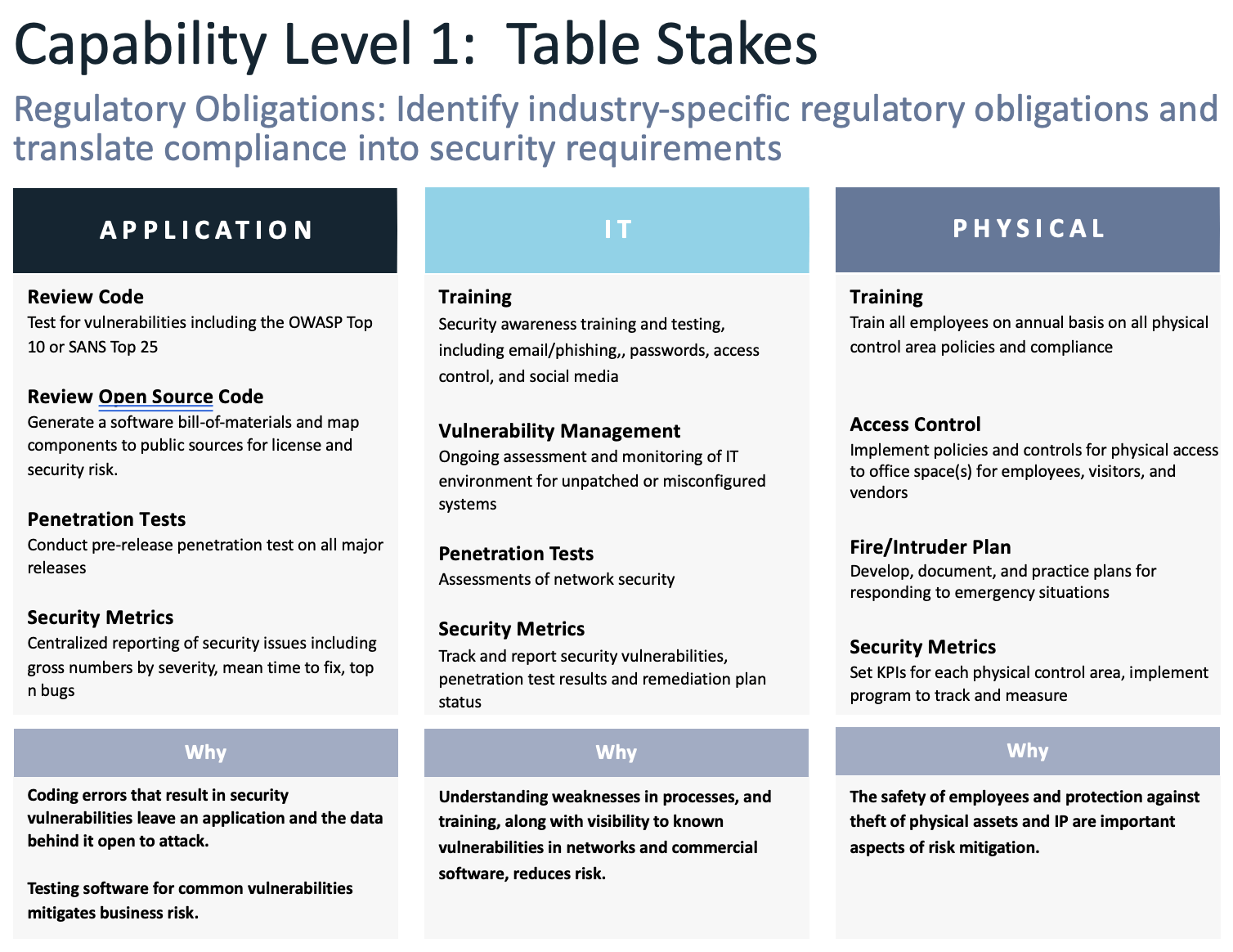
The bottom line to enabling and regulating a high-performance security practice is protecting customers, revenue, and assets. Ensuring you have a solid view of your security requirements and risks is critical to your business's success.